By Umang Dayal
July 4, 2025
Borders today are no longer just physical boundaries; they are high-stakes frontlines where technology, security, and humanitarian realities collide. From airports and seaports to remote terrain and refugee corridors, the task of maintaining secure, sovereign borders has become more complex than ever.
Traditional surveillance tools such as CCTV cameras, patrols, and physical inspections can only go so far. They’re limited by human attention, constrained by geography, and often reactive rather than preventative.
That’s why security agencies are increasingly turning to artificial intelligence, and in particular, computer vision solutions: a branch of AI that enables machines to interpret visual data with speed and precision. From identifying forged documents at immigration checkpoints to spotting unusual behavior along unmonitored border zones, it’s transforming how nations protect their perimeters.
This blog explores computer vision applications in defense, particularly how it is enhancing border security and countering terrorism across different nations.
The Evolving Landscape of Border Threats
In the current geopolitical climate, borders are more than lines on a map; they are dynamic spaces where national security, humanitarian concerns, and geopolitical tensions intersect.
The rise in global displacement due to conflict, climate change, and economic disparity has created a surge in migration flows that often overwhelm existing border control infrastructures. Smuggling syndicates and extremist groups have become adept at exploiting legal and physical blind spots, using forged documents, altered travel routes, and digital deception to bypass traditional checkpoints.
However, traditional border surveillance systems are struggling to keep pace. Reliant on static infrastructure, manual inspections, and human vigilance, these systems often operate with limited situational awareness and response time. Even when supported by basic monitoring technologies like CCTV, their effectiveness is constrained by the volume of data and the cognitive limits of human operators. This gap between the volume of threats and the capability to monitor them in real-time highlights the limitations of human-dependent systems.
To effectively respond to evolving threats, modern border security requires tools that can process vast streams of data, detect anomalies instantly, and operate continuously without fatigue. This operational need sets the stage for advanced technologies, particularly computer vision, to play a key role in building a more secure and responsive border environment.
Computer Vision in Defense & National Security
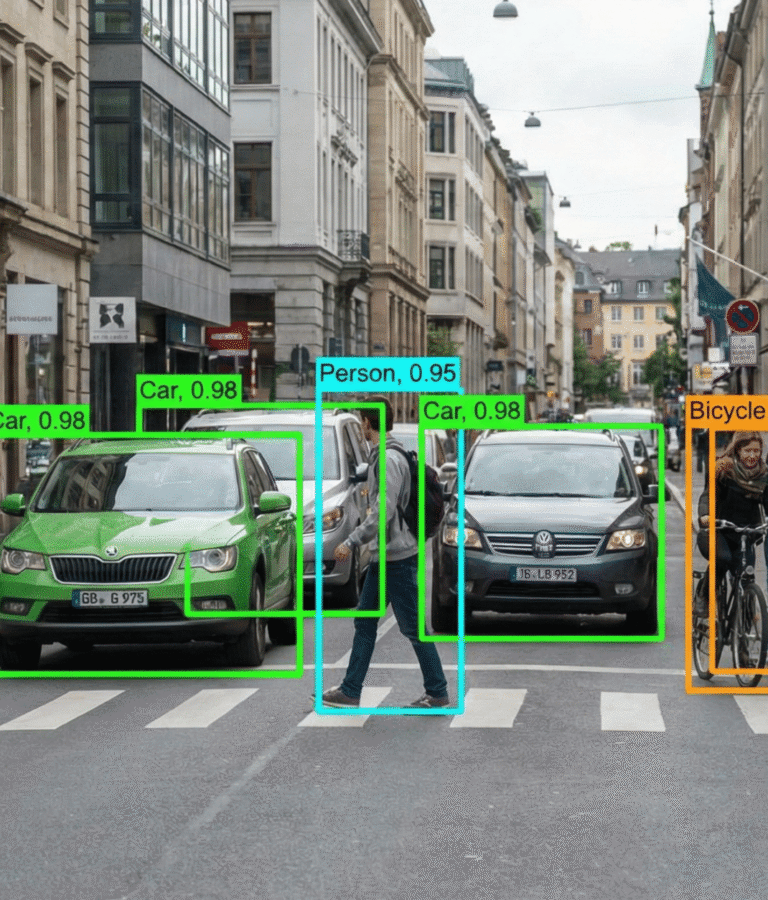
Computer vision, a rapidly evolving branch of artificial intelligence, allows machines to interpret and make decisions based on visual inputs such as images and video. In simple terms, it gives computers the ability to “see” and analyze the visual world in ways that were previously limited to human perception. When applied to border security, this technology enables the automated monitoring of people, vehicles, and objects across diverse environments such as airports, seaports, land crossings, and remote border zones.
What makes computer vision particularly effective in border operations is its real-time responsiveness, scalability, and consistency. It can process hundreds of camera feeds simultaneously, flag anomalies within seconds, and track movements with precision across large, complex terrains. Whether it is a crowded international terminal or a remote desert checkpoint, computer vision can adapt to varying conditions without compromising performance.
In modern deployments, computer vision is rarely used in isolation. It is often integrated with other data sources such as biometric sensors, drones, satellite imagery, and centralized surveillance systems. This fusion of data enhances decision-making by providing border authorities with a comprehensive, real-time operational picture. For example, a drone might capture live video of a remote area, which is then analyzed by computer vision software to detect unauthorized crossings, unusual behavior, or potential threats.
Beyond detection, these systems support intelligent responses, such as AI can prioritize alerts, reduce false positives, and even assist in forensic investigations by automatically tagging and retrieving relevant footage.
Key Applications of Computer Vision in Defense: Border Security & Counter-Terrorism
Computer vision is no longer experimental in border management; it is actively deployed in various operational contexts. The following subsections outline the most impactful applications currently being used or piloted.
Facial Recognition and Identity Verification
Biometric Matching Against Global Watchlists
One of the most established uses of computer vision at borders is facial recognition. At checkpoints and airports, systems scan travelers’ faces and automatically match them against government databases such as Eurodac in the European Union or biometric records maintained by the U.S. Department of Homeland Security. These tools can identify individuals flagged for criminal activity, prior deportations, or affiliations with terrorist organizations, significantly reducing the window of risk for unauthorized entry.
Operational Integration at Checkpoints and eGates
Facial recognition is frequently embedded into automated systems such as eGates, which speed up immigration procedures while maintaining security. These systems compare live images to biometric data stored in passports or digital ID chips. Their accuracy has improved significantly with the advent of deep learning models trained on diverse datasets, resulting in reduced error rates even in challenging conditions such as low light or partial face visibility.
Behavioral Anomaly Detection
Tracking Movement Patterns in Real Time
Beyond verifying identities, computer vision is increasingly used to monitor and assess behaviors at border zones. AI models trained on large volumes of surveillance footage can identify movement patterns that deviate from normal flow. For example, a person lingering unusually long near a restricted area, repeatedly circling a checkpoint, or moving against the typical flow of traffic may trigger automated alerts for further inspection. This continuous, context-aware monitoring supports early detection of suspicious activity that could signal trafficking, smuggling, or reconnaissance.
Detecting Subtle Signs of Risk or Evasion
Modern anomaly detection models go beyond simple motion detection. By analyzing posture, gait, pace, and trajectory, these systems can flag micro-behaviors that might be imperceptible to human observers. In high-traffic settings like ports of entry or transit hubs, where human attention is stretched thin, this capability acts as a powerful early-warning system. It also supports crowd control by alerting security teams to potential threats without disrupting the flow of legitimate travelers.
Document Fraud Detection
Automated Verification of Travel Documents
Border authorities routinely face attempts to cross borders using forged or altered documents. Computer vision systems now play a vital role in countering document fraud by automating the inspection of passports, visas, and identity cards. These systems use high-resolution image analysis to detect inconsistencies such as tampered photos, font anomalies, irregular seals, or microprint alterations, details that can often escape the notice of a human inspector, especially under time pressure.
Integration with eGates and Kiosks
This functionality is increasingly embedded within automated immigration infrastructure such as self-service kiosks and eGates. When a traveler presents a document, computer vision algorithms instantly analyze its authenticity and cross-check the information with backend databases. This not only improves security but also reduces congestion at border control points by accelerating processing for legitimate travelers.
Enhancing Trust Through Standardization
Several nations are adopting machine-readable travel documents with standardized security features to support these AI-based validation processes. In the EU, for instance, updated Schengen regulations mandate electronic document verification systems at major entry points. These systems rely heavily on computer vision to ensure that the document format, biometric photo, and embedded chip data align without requiring manual intervention.
Surveillance and Situational Awareness
Monitoring Expansive Border Zones with Computer Vision
Maintaining comprehensive situational awareness across thousands of miles of border terrain is a persistent challenge for security agencies. Computer vision addresses this gap by enabling automated, high-volume analysis of video feeds from fixed cameras, mobile units, and aerial platforms. Whether monitoring a remote desert crossing or a busy international terminal, these systems provide uninterrupted visibility and real-time analysis across vast and often inaccessible regions.
Real-Time Analysis from Drones and Satellites
Unmanned aerial vehicles (UAVs) and satellite imagery have become critical tools in border surveillance. When paired with computer vision, these platforms transform into intelligent reconnaissance systems capable of detecting human activity, vehicles, or unusual heat signatures with precision. For example, a drone equipped with infrared cameras can scan terrain at night and relay visual data to AI models that identify movement patterns inconsistent with legal crossings.
Geo-Tagged Threat Detection and Prioritization
What sets computer vision systems apart is their ability to geo-tag detections and prioritize alerts based on threat level. If a group of individuals is detected moving toward a restricted area, the system can not only flag the event but also provide coordinates, estimated numbers, and direction of movement. This enables border patrol units to respond more efficiently and with better context. Such capabilities reduce the risk of false alarms and optimize resource allocation during incident response.
Read more: Top 10 Use Cases of Gen AI in Defense Tech & National Security
Conclusion
Over the past two years, we have seen a shift from experimentation to real-world implementation. From facial recognition systems at airports to drone-based perimeter surveillance and anomaly detection tools at remote crossings, computer vision is no longer a future promise; it is a present reality. These technologies enable faster, more accurate, and more scalable responses to a range of threats, from identity fraud to human trafficking and organized terrorism.
The future of secure borders will be defined not just by how well we deploy technology, but by how wisely we govern it.
From facial recognition to object detection and geospatial analysis, DDD delivers the data precision that mission-critical applications demand, at scale, with speed, and backed by a globally trusted workforce.
Let DDD be your computer vision service partner for building intelligent and more secure applications. Talk to our experts!
References:
Bertini, A., Zoghlami, I., Messina, A., & Cascella, R. (2024). Flexible image analysis for law enforcement agencies with deep neural networks. arXiv. https://arxiv.org/abs/2405.09194
EuroMed Rights. (2023). Artificial intelligence in border control: Between automation and dehumanisation [Presentation]. https://euromedrights.org/wp-content/uploads/2023/11/230929_SlideshowXAI.pdf
IntelexVision. (2024). iSentry: Real-time video analytics for border surveillance [White paper]. https://intelexvision.com/wp-content/uploads/2024/08/AI-in-Border-Control-whitepaper.pdf
Wired. (2024, March). Inside the black box of predictive travel surveillance. https://www.wired.com/story/inside-the-black-box-of-predictive-travel-surveillance
Border Security Report. (2023). AI in border management: Implications and future challenges. https://www.border-security-report.com/ai-in-border-management-implications-and-future-challenges
Frequently Asked Questions (FAQs)
1. How do computer vision systems at borders handle poor image quality or environmental conditions?
Computer vision models used in border environments are increasingly trained on diverse datasets that include images in low light, poor weather, and obstructions such as face masks or sunglasses. Infrared and thermal imaging can also be integrated to improve detection accuracy during nighttime or in remote terrains. However, edge cases still present challenges and system performance often depends on sensor quality and environmental calibration.
2. Can computer vision help with the humanitarian aspects of border management?
Yes, there are emerging applications aimed at improving humanitarian outcomes. For example, computer vision is being tested to detect signs of distress among migrants crossing hazardous terrain, identify trafficking victims in crowded transit hubs, or monitor detention conditions. However, these use cases remain experimental and face ethical scrutiny, particularly around consent and unintended consequences.
3. How do border agencies train staff to work with AI-based surveillance systems?
Training programs are evolving to include modules on AI literacy, system interpretation, and human-in-the-loop decision-making. Border agents are trained not just to monitor alerts but to understand system limitations, verify results, and escalate cases responsibly. Some agencies also conduct scenario-based simulations to prepare staff for interpreting machine-generated intelligence in real time.